$125,600 =
The average amount a company loses to a Business Email Compromise (BEC) attack
Business Email Compromise (BEC) is one of the most financially damaging online crimes. With losses topping more than $2.7 billion last year and a year-over-year increase in attacks of 14.5%, BEC is a significant threat.
What is BEC?
In a BEC scam, criminals send an email message that appears to come from a known source making a legitimate request, like these examples:
- A vendor your company regularly deals with sends an invoice with an updated mailing address or account information.
- A company CEO asks her assistant to purchase dozens of gift cards to send out as employee rewards. She asks for the serial numbers so she can email them out right away.
- A homebuyer receives a message from his title company with instructions on how to wire his down payment.
Versions of these scenarios happened to real victims. All the messages were fake. And in each case, thousands—or even hundreds of thousands—of dollars were sent to criminals instead.
How BEC Works
In this graphic provided by the Federal Bureau of Investigation (FBI) a BEC attack is conducted through careful research to identify targets, groom company representatives, make the request, and finally, secure a fraudulent payment.
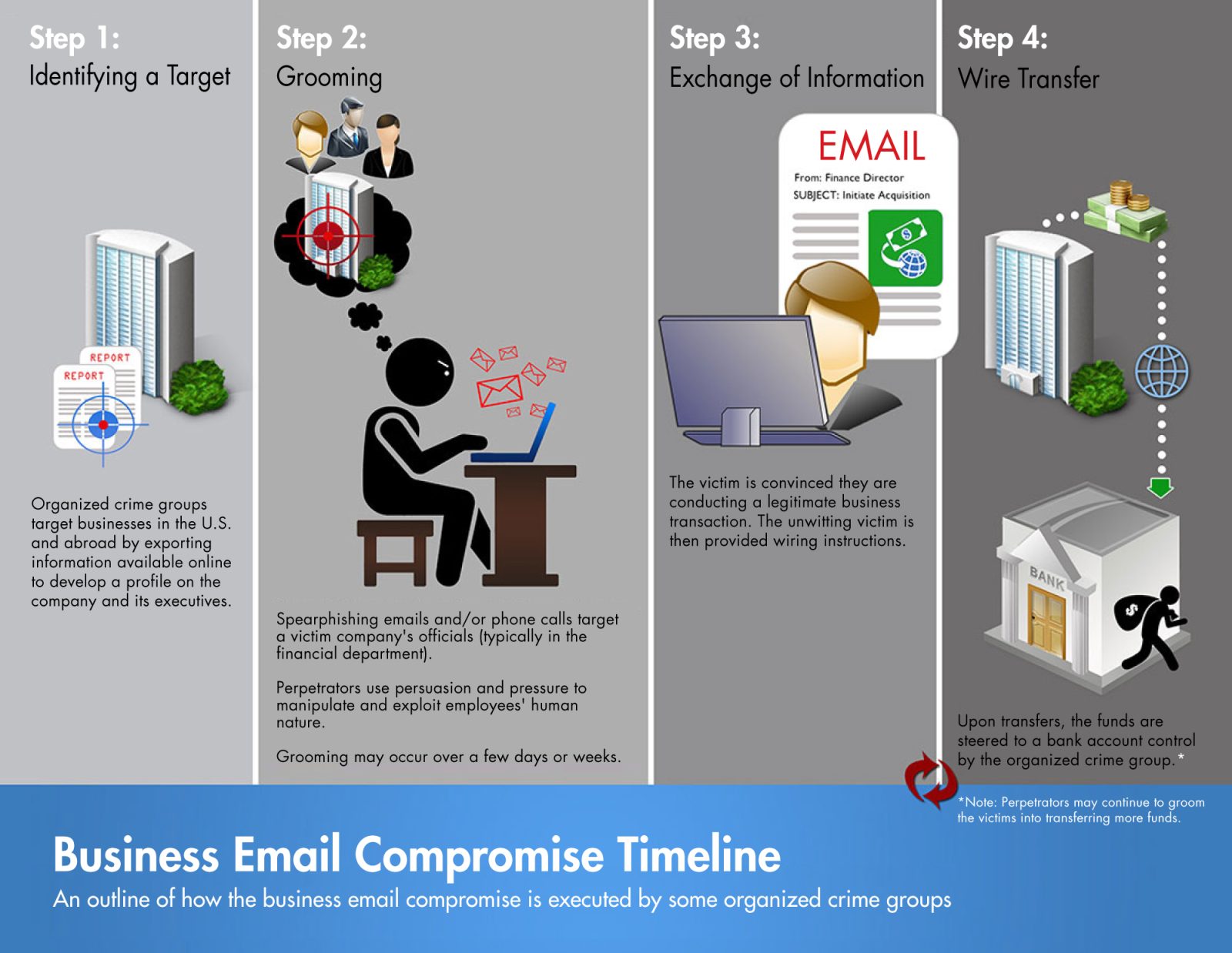
Examples of some of the more damaging BEC attacks can be found here.
The ABCs of Avoiding BEC Scams
Scammers do their homework to make their communications sound believeable. They may research company executives’ social media accounts and reference company posts to make their demands sound more realistic.
But in most cases, breaking up a BEC attack is as simple as picking up the phone to verify instructions or reading between the lines to see if an email really “sounds like” the person you know. BEC attacks are preventable. The ABCs below provide a good start for minimizing your company’s risk.
A
Avoid
- Do not use free web-based email accounts or personal email accounts for business – Don’t use free web-based email accounts for business or get in the habit of using personal email accounts to send business emails. Stick to your corporate email account, which should have more stringent security protocols.
- Avoid replying to emails – Don’t REPLY, use FORWARD instead. Forwarding an email requires you to manually type the address or select a known, trusted email address from a list. This eliminates a habit BEC attackers depend on to pull off their scams.
B
Be proactive
- Implement multi-factor authentication for your business email – MFA makes it much more difficult for cybercriminals to even gain access to an email account that could be used to commit fraud.
- Secure your company domain – BEC attacks often use spoofed domains. Registering domain names similar to your company’s will help prevent the email spoofing at the heart of many successful BEC attacks.
C
Check and double-check
- Know your customers, fellow employees, and vendors – If something seems off, it probably is. Did a trusted vendor you talked to just last week suddenly email you to say they’ve moved and to send checks to a new location? Is your normally friendly CEO suddenly sending demanding, high-pressure emails requiring money be wired within the hour? Always double-check requests that seem unusual.
- Make the call – Don’t email, pick up the phone and call your customer, co-worker, or vendor to verify any unusual requests. Use a known phone number (not one from an email) to verify that a request is legit.
As is the case with most cybercrimes, it’s much easier to prevent a BEC attack than to recover from one. In addition to the financial loss, victims of a BEC attack can end up tied up in lawsuits with customers, vendors, and insurers for years. The cost in time, resources, and reputation warrants taking a few extra seconds to follow the ABCs and keep your business safe.
